Cyber security remediation is a methodical strategy to identify and mitigate information technology security risks and vulnerabilities. It is a strategy aimed at assisting you in identifying problems before they are discovered by malicious actors.
Companies employ a wide range of techniques and defenses to protect themselves from malicious actors on the internet. These tools and defenses include things like intrusion prevention systems, intrusion detection systems, and other logging tools. In the early stages of software development, several SAST and other tools are being used to detect software flaws that have not yet been discovered.
As companies who do not deploy proper protection are considered “soft targets” by attackers, cyber security remediation measures must be implemented in order to preserve the organization’s data and assets.
Remediation Tips for Cyber Security
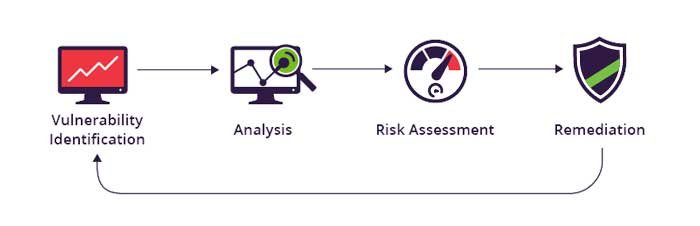
There are numerous remediation strategies that may be implemented by an organization in order to protect itself from cyber threats. Let’s talk about them.
Performing Vulnerability and Risk Assessment
Each organization employs a variety of different sorts of dependencies and information technology equipment. Nonetheless, it is always necessary for organizations to keep a software bill of materials (SBOM) that lists the software components that are currently in use within the organization. It is always necessary to conduct an appropriate IT audit of each piece of equipment that is employed in the organization.
Companies employ a variety of tools, such as SAST and DAST tools, to examine the information technology systems of their organizations. In addition, these solutions automatically execute vulnerability assessments on all assets owned or controlled by the organization and subsequently communicate their findings to the organization. As soon as they receive the report, they can begin working on addressing the vulnerabilities that have been identified and patching them.
Establish the Incident Response and Monitoring System

The incident response and monitoring systems used by each organization are key components of the organization’s overall operation. The fact that a considerable number of unprotected laptops, smartphones, and other internet-connected devices are connected to a company’s network makes this an important consideration. Your company’s data breach risk increases proportionately to the number of unmonitored endpoints in use. This is especially true in cases where security is not a high priority for the organization.
Every time something occurs that is in violation of the policies of the concerned organization, an alert is created by the incident response system. An organization’s policies and procedures are often written down and must be followed at all times. One or more Cloudtrail actions may be prohibited by an organization. As a result, if any individual inside the organization conducts any of these actions, an incident with an alert will be created, prompting the security team to take appropriate action.
Also, don’t forget to read about: Five Trends Impacting Industrial Automation Cybersecurity and How a Standards-Based Approach is a Solution
Establish Network Access Controls
Once you have evaluated your assets and determining high-priority areas where security is a must and needs to be provided, the next step is to implement network access controls to help reduce the system’s likelihood of being targeted by cybercriminals. The usage of security technologies such as a zero trust architecture, which analyses trust and user access privileges on an as-needed basis based on the job of each user, is becoming increasingly popular among companies.
Organizations are now isolating their high-priority assets in order to protect them from being compromised by low-priority or vulnerable assets, which was formerly the case. Even so, they are putting two-factor authentication and other controls on these devices and assets in order to rectify the unlawful access to those devices and resources.
Conclusion
With IT becoming a more dynamic environment, it is critical that all rules and guidelines be adhered to. There should be no deviations from the established security controls or procedures. Because an organization has a large amount of sensitive data, it should employ a variety of data protection techniques to ensure that users can place their trust in the company.



